#API Fundamentals Of Auditing
Explore tagged Tumblr posts
Text
A Comprehensive Guide to Blockchain-as-a-Service (BaaS) for Businesses
In today's digital landscape, a blockchain app development company plays a crucial role in transforming industries with decentralisation, immutability, and transparency. However, building and managing a private blockchain network can be complex and costly, which deters many businesses. Blockchain-as-a-Service (BaaS) simplifies this by allowing businesses to leverage blockchain without the challenges of infrastructure development.
This comprehensive blog covers the hurdles businesses face when adopting blockchain, how BaaS can bridge these gaps, and why it is a game-changer for various sectors.
I. Challenges for Businesses in Blockchain Adoption
Despite the undeniable potential of blockchain technology, businesses face several significant challenges when contemplating its adoption:
Limited Internal Expertise: Developing and maintaining a private blockchain network requires a skilled team with deep blockchain knowledge, which is often lacking in many organisations.
High Cost: The infrastructure investment and ongoing maintenance fees associated with blockchain can strain budgets, especially for small and medium-sized businesses (SMBs).
Integration Complexities: Integrating a blockchain network with existing enterprise systems can be challenging, requiring seamless data flow and compatibility between the blockchain system and legacy infrastructure.
II. Understanding BaaS and Its Operational Fundamentals
Blockchain-as-a-Service (BaaS) simplifies the development and deployment of blockchain applications by providing a cloud-based platform managed by third-party providers. The BaaS market, valued at $1.5 billion in 2024, is projected to grow to $3.37 billion by 2029, reflecting a robust 17.5% CAGR.
Key Components of BaaS
Cloud-Based Infrastructure: Ready-to-use blockchain infrastructure hosted in the cloud, eliminating the need for businesses to set up and maintain their networks.
Development Tools and APIs: Access to a suite of tools and APIs to create and deploy blockchain applications quickly.
Platform Support: Compatibility with various blockchain protocols such as Ethereum, Hyperledger Fabric, and Corda, offering flexibility to businesses.
Managed Service Model: Providers handle tasks like network maintenance, security updates, and scalability.
Pay-as-you-go Pricing Model: Reduces upfront investment and operational costs associated with blockchain software development.
III. Business Benefits of Blockchain as a Service
Adopting BaaS offers numerous advantages, including:
Enhanced Scalability: Businesses can easily scale their blockchain network as their needs grow.
Increased Efficiency: Eliminates intermediaries and streamlines transactions, improving productivity.
Enhanced Transparency: Tamper-proof records of transactions foster trust and improve auditability.
Reduced Costs: The pay-as-you-go model eliminates large upfront investments.
Improved Security: Built on secure cloud infrastructure with robust encryption protocols.
Enhanced Customer Engagement: Facilitates secure and transparent interactions with customers, building trust and loyalty.
IV. Industry-wise Key Use Cases of Blockchain as a Service
BaaS is transforming business operations across various industries:
Finance: Streamlines trade finance, secures cross-border payments, and enhances KYC and AML compliance.
Supply Chain Management: Improves transparency and traceability of goods, automates logistics processes, and reduces counterfeiting risks.
Healthcare: Facilitates secure sharing of patient data and tracks the provenance of pharmaceuticals.
Government: Enhances transparency with secure citizen identity management and verifiable voting systems.
V. Region-wise Adoption of BaaS
The BaaS market is experiencing rapid growth worldwide:
North America: Leading with over 35% of global revenues, driven by early adoption.
Europe: Countries like Germany, the UK, and France are at the forefront.
Asia-Pacific: China, India, Japan, and South Korea are key contributors.
Rest of the World: Growing adoption in South & Central America, the Middle East, and Africa.
VI. Why Choose a Prominent BaaS Provider?
Opting for a blockchain app development company that offers BaaS can significantly impact the success of your blockchain initiatives:
Specialised Expertise: Providers possess in-depth knowledge and experience in blockchain technology.
Cost Efficiency: Eliminates the need for in-house infrastructure investment and maintenance.
Time Savings: Accelerates the development process and reduces time-to-market.
Scalability and Flexibility: Offers scalable solutions that can adapt to business growth.
Risk Mitigation: Providers handle security, maintenance, and updates.
Conclusion
By adopting Blockchain-as-a-Service (BaaS), businesses can simplify blockchain integration and focus on innovation without the complexities of managing infrastructure. Systango, a leading blockchain app development company, offers tailored BaaS solutions that help businesses leverage blockchain technology for enhanced efficiency, scalability, and security. As one of the top , Systango also excels in integrating AI solutions to drive business growth and efficiency.
Original Source - https://systango.medium.com/a-comprehensive-guide-to-blockchain-as-a-service-baas-for-businesses-5c621cf0fd2f
2 notes
·
View notes
Text
How Automation and Integration Are Shaping the Future of ESG

Artificial intelligence, machine learning, IoT sensors, blockchain ledgers, and cloud-scale analytics are rapidly reshaping the way organisations collect, verify, and communicate environmental, social, and governance information. When these tools are woven into a single, automated fabric, a task that once relied on spreadsheets and manual checks turns into a real-time risk-management engine—cutting costs, easing compliance pressure, and surfacing growth opportunities that used to stay hidden.
Why the classic ESG playbook is falling short
Most companies still anchor their reports on fundamentals such as Scope 1 emissions, electricity consumption, or workforce-diversity ratios. Essential as those metrics are, they paint only part of the picture. Disclosures arrive late, calculation methods differ by industry, and boiler-plate wording makes peer comparison difficult. The result is unreliable insight, frustrated investors, and growing regulatory exposure.
Enter alternative data and AI-powered insight
Bridging that gap demands sources far beyond the annual report. Alternative data spans satellite imagery estimating methane plumes, credit-card exhaust hinting at supply-chain resilience, geolocation traces mapping factory activity, mobile-app usage reflecting customer sentiment, and social-media feeds tracking reputation shifts hour by hour. When these streams flow into AI models, they generate granular, near-real-time signals that sharpen risk scoring, flag misconduct early, and highlight positive impacts that traditional metrics overlook.
Automation then amplifies the payoff. APIs pipe third-party feeds into an internal ESG lake, cleansing rules standardise formats, taxonomy tags map fields to evolving regulations, and templates generate regulator-ready disclosures with a click. What was reactive becomes predictive; what was a cost centre becomes a value generator.
A live example: Neoimpact’s ESG Intelligence Dashboard
Neoimpact demonstrates how an integrated approach works in practice. Its cloud platform fuses core metrics with dozens of alternative feeds, then layers AI analytics on top. Users can benchmark companies across sectors and regions, track score movements over time, and drill into individual risk drivers—whether that is an uptick in deforestation alerts or a spike in workforce-sentiment negativity. Asset managers gain a clearer view of portfolio exposure, while compliance teams secure auditable trails that stand up to tighter regulatory scrutiny.
Three priorities for the road ahead
Invest in unified ESG technology. Point solutions trap data in silos. Platforms that combine ingestion, validation, analytics, and disclosure collapse cost and accelerate insight.
Broaden the data lens. Fundamental metrics remain foundational, but firms overlaying them with curated alternative datasets will out-perform peers on transparency and foresight.
Automate end-to-end. From sensor deployment and API ingestion to AI scoring and one-click disclosure, automation converts episodic reporting into continuous oversight—reducing risk, protecting brand equity, and freeing talent for strategic work.
The payoff
As stakeholder expectations rise and rulebooks such as the CSRD and the SEC’s climate-disclosure mandate tighten, companies that treat ESG as an after-thought will find the cost of capital climbing. Those that embrace next-generation tech, richer data, and fully automated workflows will not only comply with less effort; they will embed sustainability into everyday decision-making and unlock durable, long-term value.
The verdict is clear: integrated, AI-driven ESG technology is shifting from nice-to-have to business essential. Acting now lets forward-looking firms turn complexity into competitive advantage—lowering cost, mitigating risk, and positioning themselves for a future where responsible performance is inseparable from financial success.
0 notes
Text
Ensuring Resilient Security for Autonomous AI in Healthcare
New Post has been published on https://thedigitalinsider.com/ensuring-resilient-security-for-autonomous-ai-in-healthcare/
Ensuring Resilient Security for Autonomous AI in Healthcare


The raging war against data breaches poses an increasing challenge to healthcare organizations globally. As per current statistics, the average cost of a data breach now stands at $4.45 million worldwide, a figure that more than doubles to $9.48 million for healthcare providers serving patients within the United States. Adding to this already daunting issue is the modern phenomenon of inter- and intra-organizational data proliferation. A concerning 40% of disclosed breaches involve information spread across multiple environments, greatly expanding the attack surface and offering many avenues of entry for attackers.
The growing autonomy of generative AI brings an era of radical change. Therefore, with it comes the pressing tide of additional security risks as these advanced intelligent agents move out of theory to deployments in several domains, such as the health sector. Understanding and mitigating these new threats is crucial in order to up-scale AI responsibly and enhance an organization’s resilience against cyber-attacks of any nature, be it owing to malicious software threats, breach of data, or even well-orchestrated supply chain attacks.
Resilience at the design and implementation stage
Organizations must adopt a comprehensive and evolutionary proactive defense strategy to address the increasing security risks caused by AI, especially inhealthcare, where the stakes involve both patient well-being as well as compliance with regulatory measures.
This requires a systematic and elaborate approach, starting with AI system development and design, and continuing to large-scale deployment of these systems.
The first and most critical step that organizations need to undertake is to chart out and threat model their entire AI pipeline, from data ingestion to model training, validation, deployment, and inference. This step facilitates precise identification of all potential points of exposure and vulnerability with risk granularity based on impact and likelihood.
Secondly, it is important to create secure architectures for the deployment of systems and applications that utilize large language models (LLMs), including those with Agentic AI capabilities. This involves meticulously considering various measures, such as container security, secure API design, and the safe handling of sensitive training datasets.
Thirdly, organizations need to understand and implement the recommendations of various standards/ frameworks. For example, adhere to the guidelines laid down by NIST’s AI Risk Management Framework for comprehensive risk identification and mitigation. They could also consider OWASP’s advice on the unique vulnerabilities introduced by LLM applications, such as prompt injection and insecure output handling.
Moreover, classical threat modeling techniques also need to evolve to effectively manage the unique and intricate attacks generated by Gen AI, including insidious data poisoning attacks that threaten model integrity and the potential for generating sensitive, biased, or inappropriately produced content in AI outputs.
Lastly, even after post-deployment, organizations will need to stay vigilant by practicing regular and stringent red-teaming maneuvers and specialized AI security audits that specifically target sources such as bias, robustness, and clarity to continually discover and mitigate vulnerabilities in AI systems.
Notably, the basis of creating strong AI systems in healthcare is to fundamentally protect the entire AI lifecycle, from creation to deployment, with a clear understanding of new threats and an adherence to established security principles.
Measures during the operational lifecycle
In addition to the initial secure design and deployment, a robust AI security stance requires vigilant attention to detail and active defense across the AI lifecycle. This necessitates for the continuous monitoring of content, by leveraging AI-driven surveillance to detect sensitive or malicious outputs immediately, all while adhering to information release policies and user permissions. During model development and in the production environment, organizations will need to actively scan for malware, vulnerabilities, and adversarial activity at the same time. These are all, of course, complementary to traditional cybersecurity measures.
To encourage user trust and improve the interpretability of AI decision-making, it is essential to carefully use Explainable AI (XAI) tools to understand the underlying rationale for AI output and predictions.
Improved control and security are also facilitated through automated data discovery and smart data classification with dynamically changing classifiers, which provide a critical and up-to-date view of the ever-changing data environment. These initiatives stem from the imperative for enforcing strong security controls like fine-grained role-based access control (RBAC) methods, end-to-end encryption frameworks to safeguard information in transit and at rest, and effective data masking techniques to hide sensitive data.
Thorough security awareness training by all business users dealing with AI systems is also essential, as it establishes a critical human firewall to detect and neutralize possible social engineering attacks and other AI-related threats.
Securing the future of Agentic AI
The basis of sustained resilience in the face of evolving AI security threats lies in the proposed multi-dimensional and continuous method of closely monitoring, actively scanning, clearly explaining, intelligently classifying, and stringently securing AI systems. This, of course, is in addition to establishing a widespread human-oriented security culture along with mature traditional cybersecurity controls. As autonomous AI agents are incorporated into organizational processes, the necessity for robust security controls increases. Today’s reality is that data breaches in public clouds do happen and cost an average of $5.17 million , clearly emphasizing the threat to an organization’s finances as well as reputation.
In addition to revolutionary innovations, AI’s future depends on developing resilience with a foundation of embedded security, open operating frameworks, and tight governance procedures. Establishing trust in such intelligent agents will ultimately decide how extensively and enduringly they will be embraced, shaping the very course of AI’s transformative potential.
#access control#Advice#Agentic AI#agents#ai#AI AGENTS#AI in healthcare#ai security#AI systems#API#applications#approach#Attack surface#attackers#attention#autonomous#autonomous ai#awareness#Bias#breach#Business#challenge#change#chart#CitiusTech#classical#clouds#compliance#comprehensive#container
0 notes
Text
The Complete Guide to Spotfire: Analytics, Visualization, and Expert Training
Businesses want powerful gear to investigate, visualize, and interpret complicated datasets correctly. Spotfire Analyticsis one such platform that permits corporations to convert uncooked statistics into actionable insights. Whether you're looking for superior Spotfire Data Visualization, custom Spotfire Development, or professional QA Consulting Services, Tech Innovations gives complete answers to help you leverage Spotfire's full ability.
What is Spotfire Analytics?
The business intelligence and information analytics platform Spotfire Analytics comes from TIBCO via its development method. The platform gives organizations the power to study and break down significant data collections in real-time through visualization tools. Spotfire enables customers to construct interactive dashboards and predictive models alongside AI-pushed insights by way of its smooth-to-use drag-and-drop interface, which calls for minimum coding heritage.
Key Features of Spotfire Analytics:
Interactive Dashboards – Create dynamic visualizations for better decision-making.
The platform features predictive analytics capabilities along with built-in statistical tools in addition to machine learning functions.
Real-Time Data Processing – Connect to multiple data sources for live insights.
Users can enhance functionality through the implementation of R, Python, and IronPython scripts.
Spotfire Data Visualization: Turning Data into Insights
Spotfire Data Visualization stands as the most distinctive characteristic of Spotfire's system. Information systems available in Spotfire empower business users to develop various visualizations, including heat maps, scatter plots and bar charts, which expose hidden patterns.
Why Choose Spotfire for Data Visualization?
Standard users need no technical knowledge to operate this interface.
Interactive Visualizations – Drill down into data with just a few clicks.
Customizable Dashboards – Tailor reports to meet business needs.
Collaboration Tools – Share insights across teams seamlessly.
Kanika Tech Innovations helps businesses maximize their Spotfire Data Visualization potential by designing custom dashboards that align with specific business goals.
Spotfire Development: Custom Solutions for Your Business
The analytics requirements of every business are different, so Spotfire Development adapts the platform to match specific organizational needs. The development team at Kanika Tech Innovations handles all of Spotfire's development projects, which include both system integration and customized scripting work.
Spotfire Development Services Include:
Custom Scripting & Automation – The platform requires no technical expertise from users to operate its interface.
API Integrations – Drill down into data with just a few clicks.
Performance Optimization – The system enables users to create personalized dashboards according to their specific business requirements.
Cloud & On-Premise Deployment – Share insights across teams seamlessly.
Enhance Data Quality with QA Consulting Services
Accurate data functions as the fundamental base which supports successful analytics operations. Kanika Tech Innovations provides QA Consulting Services to maintain data consistency along with reliability and integrity inside Spotfire platforms.
Our QA Services Include:
Data Validation & Cleansing – The data validation and cleansing process removes both errors and duplicate data entries.
Dashboard Testing – Verifying visualizations for accuracy.
Performance Testing –The evaluation of dashboard performance provides assurance regarding efficient dashboard loading speed.
Security Audits – Protecting sensitive business data.
Expert Spotfire Training for Your Team
Organizations need proper training to fully utilize Spotfire's capabilities. Kanika Tech Innovations provides Spotfire Training programs designed for beginners and advanced users alike.
Spotfire Training Modules:
Introduction to Spotfire Analytics – Basic navigation and visualization.
Advanced Data Analysis – Predictive modeling and scripting form the advanced aspect of data analytics within Spotfire.
Dashboard Development – Building interactive reports.
Administration & Deployment – Building interactive reports.
Through experience-based training, we guarantee your team will reach maximum Spotfire capabilities to achieve better workplace performance and decisions.
Why Choose Kanika Tech Innovations?
Certified Spotfire Experts – Years of experience in analytics and BI.
Custom Solutions – Tailored to your business needs.
End-to-End Support – The company supports customers across every phase, from project launch to training completion.
Proven Track Record – The company maintains trust between customers in various business sectors, including enterprise and academic institutions.
Final Thoughts
Spotfire Analytics is a game-changer for businesses looking to harness the power of data. With Spotfire Data Visualization, custom Spotfire Development, QA Consulting Services, and expert Spotfire Training, Innovations ensures you get the most out of this powerful platform.
1 note
·
View note
Text
9 Mistakes to Avoid When Learning Web3 Development
As the demand for Web3 development continues to rise in 2025, more developers are exploring this exciting new world of decentralized technologies. However, Web3 is not just another coding skill—it requires a shift in mindset, architecture, and tools.

Whether you're new to blockchain or transitioning from Web2, avoiding common mistakes early can save you time, frustration, and even money. In this article, we’ll break down 9 common mistakes to avoid when learning Web3 development, along with practical advice to get ahead.
1. Skipping Blockchain Fundamentals
Many developers jump straight into coding smart contracts without truly understanding how blockchains work. A solid grasp of consensus mechanisms, transaction flow, gas fees, and blocks is essential.
If you don’t understand the system you’re building on, you’ll likely introduce security flaws or build inefficient applications.
2. Neglecting Smart Contract Security
One of the most critical areas in Web3 development services is smart contract security. Vulnerabilities like reentrancy attacks, integer overflows, or improper access control can cause major losses.
Before deploying anything live:
Study secure development practices
Use auditing tools like Slither or MythX
Learn from past exploit case studies
3. Focusing Only on Ethereum
Ethereum is popular, but it’s not the only chain. Developers should also explore other ecosystems like:
Polygon (Layer 2 scaling)
Solana (high throughput)
BNB Chain
Arbitrum and Optimism (Layer 2 rollups)
Modern Web3 development companies work across multiple chains to optimize performance, fees, and user experience.
4. Ignoring Web2 Skills
Many newcomers believe Web3 requires abandoning traditional web skills. In reality, you still need:
HTML/CSS
JavaScript frameworks like React or Next.js
API integration
A great dApp still needs a solid UI. Web3 solutions that ignore frontend development often end up with poor usability.
5. Not Testing Thoroughly
Failing to test smart contracts and dApps properly is a costly mistake. You should use testnets (like Sepolia, Mumbai, or Fuji) and automated testing tools to catch bugs early.
Use:
Hardhat
Foundry
Truffle
Ganache
Testing is standard practice for every successful Web3 development agency.
6. Underestimating Gas Fees
Gas fees on chains like Ethereum can fluctuate wildly. Writing inefficient code can lead to high execution costs for users.
Web 3.0 developers should optimize smart contracts and understand gas estimation to keep dApps affordable.
7. Not Understanding Token Standards
A good Web 3.0 development company should be familiar with:
ERC-20 (fungible tokens)
ERC-721 (NFTs)
ERC-1155 (multi-token standard)
Knowing when and how to use each standard is essential to creating interoperable Web3 platforms.
8. Skipping Documentation and Community Resources
The Web3 space evolves rapidly. Developers who don’t read documentation or participate in developer forums fall behind quickly.
Stay active on GitHub, Discord, and follow official docs for tools like Ethers.js, Web3.js, and The Graph.
9. Building Without Real-World Use Cases
Many developers jump into projects without solving real problems. Building “just another NFT site” with no unique value won’t succeed.
Study existing Web3 development services and identify how to innovate. Whether it’s finance, gaming, social media, or supply chains—every great project starts with a meaningful problem.
Final Thoughts
Learning Web3 development is rewarding, but it comes with its challenges. By avoiding these 9 common mistakes, you’ll set yourself up for long-term success in the decentralized space.
At Nadcab Labs, we guide startups and enterprises through successful blockchain implementation. Our experienced Web 3.0 developers and security-first mindset ensure that your project is built the right way from the start.
Whether you're building a dApp, NFT platform, or DeFi protocol, we’re here to help.
Visit us here for more:- https://www.nadcab.com/web3-development-services
Get more Blockchain and Web3 Insights with Nadcab Labs
Twitter - twitter.com/nadcablabs
LinkedIn - linkedin.com/company/nadcablabs
Facebook- facebook.com/nadcablabs
Instagram- instagram.com/nadcablabs
YouTube- www.youtube.com/@nadcablabs
#blockchain#technology#web3developmentcompany#Web3DevelopmentServices#Web3Solutions#Web3Development#Web3.0Development#Web3.0DevelopmentServices#web3.0solutions#Web3.0DevelopmentCompany#Web3developmentagency#Web3.0developer
0 notes
Text

Key Metrics To Choose the Right Transport Management Software
In a world where speed and efficiency define logistics success, choosing the right Transport Management Software (TMS) is more important than ever.
With countless options flooding the market, businesses need to focus on key performance metrics to make a smart choice.
Let’s dive in.
User Friendliness
A complex interface can hinder user adoption and delay workflows. Choose software that has simple navigation, clear layouts, and easy access to critical functions.
Mobile compatibility is advantageous, allowing your staff to manage duties both in-office and remotely. User-friendly design results in faster onboarding and higher operational productivity.
Features Comparison
When selecting transport management software, it is critical to compare fundamental features that have a direct impact on operational effectiveness. Key functionalities to look for:
User registration
Fleet optimization
Load planning
Carrier management
Document automation
Multi-modal support
Real-time analytics
Finally, comparing features assures that the software meets your current requirements and can expand as your business grows.
Inventory Management
Transport management software should integrate with inventory systems to provide real-time stock visibility. This enables you to find correct order fulfillment, eliminates the possibility of stockouts or overstocking, and enhances warehouse coordination.
Advanced inventory monitoring systems, such as barcode scanning and serial number tracking, can help to speed the receiving and dispatching procedures.
By maintaining uniform inventory levels across all locations, you can increase accuracy, reduce holding costs, and ensure on-time delivery.
Real-time Visibility & Tracking
Visibility is critical to proactive logistics management. So, you select transport management software that provides real-time shipment monitoring, estimated delivery time, and status updates can help you avoid delays and provide correct information to consumers.
Additionally, features such as GPS monitoring, geofencing notifications, and digital proof of delivery increase transparency and user trust.
Integration Capabilities
Transportation management software should integrate with ERP, WMS, CRM, and accounting systems. It should also enable third-party logistical services, payment gateways, and e-commerce platforms.
API access and pre-built connections offer easy data exchange, streamline operations, decrease manual work, and enable centralized control across all business processes.
Cost Optimization Tools
Transportation costs are a significant expense for logistics businesses. A good transport management software should incorporate cost-saving features such as route optimization, load consolidation, freight auditing, and invoice reconciliation.
These functionalities assist in identifying inefficiencies and reducing fuel, labor, and shipping charges.
Security and Compliance
Transport management software must provide strong data security and regulatory compliance. Pick solutions with role-based access, data encryption, safe cloud hosting, and compliance with regulations such as GDPR.
Features such as automatic compliance checks for driver hours, vehicle maintenance, and insurance contribute to operational transparency and audit-readiness.
Complete Support
Robust support services are required for efficient logistics operations. Choose a software provider that offers 24-hour technical support, onboarding assistance, extensive training, and a dedicated account manager.
Prompt assistance saves downtime, speeds up problem resolution, and guarantees that your team can fully utilize the platform without delays or disturbances in important logistics procedures.
Summing Up
Hope, by analyzing these key metrics, you can confidently pick the right transport management software that fits your business needs.
This will help your business to boost efficiency, reduce costs, and enhance overall logistics performance for long-term success.
Choose right now!
0 notes
Text
Top 10 Power BI Migration Best Practices: A Comprehensive Guide for 2025
Before focusing on specific Power BI migration best practices, it is essential to know that successful migration requires careful planning and a well-structured approach. Our certified Power BI experts have gathered these best practices from years of experience and many successful projects.
Key Aspects of Power BI Migration Best Practices
Implementing Power BI migration best practices requires a comprehensive approach. Let's examine how these practices can improve your organization's data analytics capabilities.
1. Strategic Migration Planning and Architecture Design
Following Power BI migration best practices, a robust migration planning methodology is the cornerstone of any successful Power BI transition. The process begins with thoroughly assessing existing reports and dashboards and creating a detailed inventory of data sources and dependencies. Organizations should develop a phased migration approach while implementing proper version control implementation strategies to maintain consistency throughout the process.
2. Optimizing Data Models and Performance
Among critical Power BI migration best practices, data model optimization plays a crucial role in ensuring optimal performance post-migration. Implementing star schema design principles serves as the foundation for efficient data modeling. This should be combined with optimized relationships and cardinality, proper DAX optimization techniques, and efficient data refresh strategies to maintain peak performance.
3. Security and Compliance Framework
Modern Power BI migration best practices emphasize that robust security testing procedures are non-negotiable in today's data-driven landscape. This includes comprehensive row-level security implementation and properly configured authentication methods. Organizations must establish thorough audit logging setup procedures while ensuring all regulatory compliance measures are met and maintained throughout the migration process.
4. Infrastructure and Environmental Preparation
Following established Power BI migration best practices, proper infrastructure preparation ensures a stable foundation for your Power BI environment. This encompasses configuring data gateways and implementing load-balancing setup mechanisms. Organizations must establish comprehensive capacity planning guidelines and resource allocation planning to support their growing data needs.
5. User Management and Access Control
Contemporary Power BI migration best practices stress that effective user access migration requires careful consideration of various aspects of security and accessibility. This includes implementing role assignment strategies and setting up workspace access control mechanisms. The management of permission inheritance and establishment of robust identity management protocols ensure secure and efficient user access management.
6. Testing and Validation Protocols
Comprehensive migration testing methods are essential for ensuring reliability and performance. This includes conducting thorough integration testing and detailed user acceptance testing. Implementing quality assurance protocols helps maintain data accuracy and consistency throughout the migration process.
7. Documentation and Knowledge Transfer
Creating detailed migration documentation is fundamental for long-term success. This encompasses developing comprehensive user training materials and establishing standard operating procedures. Technical teams should maintain detailed technical specifications and troubleshooting documentation for future reference and support.
8. System Integration and Connectivity
Successful API integration forms the backbone of seamless operation in a Power BI environment. This includes managing system connectivity and implementing custom connector migration procedures. Organizations must ensure cross-platform compatibility and proper service integration to maintain smooth operations.
9. Monitoring and Maintenance Strategy
Implementing effective post-migration monitoring ensures sustained performance and reliability. This involves setting up comprehensive performance analytics and configuring appropriate alert configuration systems. Organizations should establish robust backup procedures and implement thorough health metrics tracking for ongoing maintenance.
10. Cloud Integration and Management
Proper cloud resource management is crucial for modern deployments in today's digital landscape. This includes seamless Azure integration and implementation of robust cloud security setup protocols. Organizations must establish comprehensive disaster recovery protocols and maintain efficient tenant configuration management.
Why Choose DataTerrain for Your Power BI Migration
At DataTerrain, we understand that implementing Power BI migration best practices requires expertise, experience, and a proven methodology. Our team of certified professionals has successfully guided numerous organizations through their Power BI migration journey, ensuring optimal performance, security, and user adoption.
DataTerrain stands out in the industry with over 15 years of data analytics expertise backed by certified Power BI professionals who understand the nuances of successful migrations. Our proven migration methodology, comprehensive support and training, and custom solutions are tailored to meet your organizational needs.
0 notes
Text
Regulatory Compliance and Security in DMT
Security and regulatory compliance are fundamental to any Domestic Money Transfer system. In India, DMT services must adhere to RBI regulations, including KYC (Know Your Customer) norms, transaction monitoring, and fraud prevention protocols. KYC can be minimal, such as mobile number verification, for low-value transactions, or more stringent—like Aadhaar or PAN-based authentication—for higher amounts. All API interactions are encrypted using SSL/TLS to ensure data security and integrity. Platforms are also required to maintain complete audit trails of every transaction, including time stamps and device identifiers, to support accountability and legal compliance. Advanced systems also implement AI-based fraud detection and real-time alerting mechanisms to catch suspicious activity early. These compliance measures not only protect users but also strengthen the reliability and trustworthiness of the platform.
0 notes
Text
Common Mistakes Students Make in QA QC Courses and How to Avoid Them
Quality Assurance (QA) and Quality Control (QC) are crucial components in various industries, particularly in engineering fields. For mechanical engineering students, mastering these concepts can open doors to a range of technical and supervisory roles. However, many students enrolling in QA QC courses often repeat avoidable mistakes that hinder their learning and future career prospects. Understanding these common pitfalls can help students make the most of their training and stand out in a competitive job market.
1. Underestimating the Basics
Many students dive into QA QC training with a focus on advanced topics, neglecting the fundamental principles. Concepts like standards, inspection techniques, and calibration are often glossed over, despite being essential building blocks. Skipping the basics can lead to confusion later when dealing with real-world scenarios.
How to avoid it: Ensure that you have a strong grasp of basic mechanical engineering concepts before starting the course. Ask questions, revisit your academic notes, and clarify any doubts early on.
2. Relying Solely on Theory
QA QC is a field that demands both theoretical knowledge and practical skills. Students who focus only on classroom lessons without engaging in hands-on training often struggle in actual inspection or documentation tasks.
How to avoid it: Choose institutions that offer well-structured mechanical QA QC courses in Trivandrum with lab sessions, site visits, or internships. Practice using industry-standard tools and software wherever possible.
3. Ignoring Industry Standards and Codes
Understanding ISO, ASME, API, and other international codes is vital for QA QC professionals. Yet, many students don’t pay enough attention to these standards, thinking they can always refer to them later.
How to avoid it: Start familiarizing yourself with relevant codes from day one. Try to interpret how they apply in practical scenarios and stay updated with changes.
4. Not Working on Communication Skills
QA QC roles often involve interacting with production teams, auditors, and clients. Poor communication can lead to misunderstandings, errors, or failure in audits.
How to avoid it: Work on your report-writing and verbal communication skills. Being able to clearly explain inspection results and documentation is a significant asset.
5. Skipping Mock Interviews and Soft Skills Training
Many students are technically sound but falter during job interviews due to lack of preparation or confidence.
How to avoid it: Participate in mock interviews and soft skills sessions. If your training center for mechanical QA QC courses in Trivandrum offers placement support, make full use of those resources.
Conclusion
Success in QA QC isn’t just about mastering tools or memorizing codes; it’s about combining technical expertise with practical application and communication. By avoiding these common mistakes, students can gain a solid foundation and increase their chances of landing a rewarding job in the industry. Take your training seriously, stay curious, and always be willing to learn and improve.
0 notes
Text
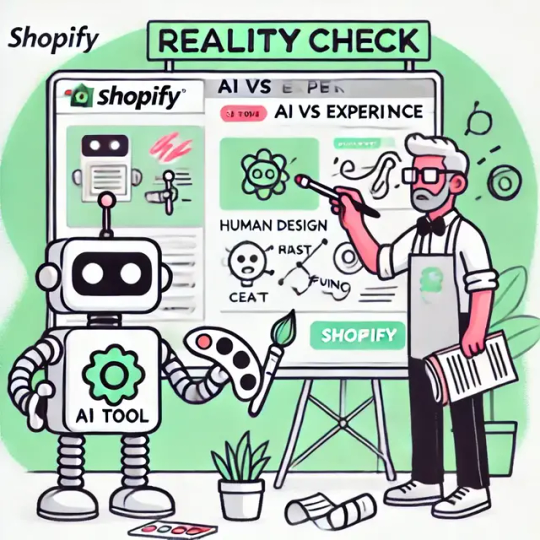
The Reality of AI in Shopify Product Design
Discover the truth about AI in Shopify product design and why human expertise is irreplaceable.
Source: https://cro.media/insights/ux-ui/ai-powered-product-design-conversion-optimization/
In today's market, AI is often touted as a game-changer for product design, especially for Shopify websites. However, the reality is that AI tools are not the magic solution they are often advertised to be. While they can provide some useful features, they are far from replacing the need for human expertise in improving conversion rates.
The Overhyped Promise of AI
Many site builders and analytics tools now market their features as "AI-powered," but in most cases, these tools have not fundamentally changed. The addition of AI often means some session analysis and summarization, which can give a recap but never the full, accurate picture. This can add extra noise and make it harder to understand what's really happening on your website.
For example, if you decide to save money by not hiring an experienced analytics professional and instead rely on an AI tool like Clarity's AI summarize feature, you might end up with a smart-looking but inaccurate analysis. It's like hiring someone with a good vocabulary but no real skills or experience, adding noise and hiding reality.
I see AI powered Shopify Apps
Want to a good advise, at this point change the mindset, whenever you see AI powered, AI driven, AI anything, just think of it as a marketing buzzword. It's not that AI is bad, it's just that they don't have anything so suggest, the just wrapped their shitty product with open ai API wrapper and call it AI powered. Want to filter - you see ai, consider it as last option. Don't waste your time on it.
The Myth of AI-Driven Product Design
When it comes to product design, particularly for Shopify websites, there's no real tool that can design a high-converting site for you. AI tools can at best provide some nice-looking, generic designs. If your website currently looks terrible, a new design might convert better simply due to common sense improvements, not because of any AI magic.
In reality, tools like Framer AI generate standard designs and use AI as a marketing buzzword. They don't have anything to do with true AI capabilities. As a Shopify agency specializing in improving conversion rates for DTC brands and other e-commerce sites, we can tell you that the best way to improve your product design is to start by analyzing successful competitors.
The Importance of Human Expertise
First, diagnose your website by ordering a Shopify CRO audit to identify what's wrong. Then, implement improvements day by day. There is no magic pill, and AI-powered product designs are just marketing hype. The sooner you understand that AI is amazing but not everything, the better you'll be able to balance your resources and not fully rely on AI for design.
The Reality of AI-Powered Site Builders
We deal with this every day when clients come to us saying they've found an AI tool that can make landing pages and automatically convert them into Shopify pages. After spending two weeks and a lot of money on tokens without getting the job done, they realize they still need human and expert help. AI builders often mess up the entire website, making the product design even worse, heavier, and requiring a complete redo of the work.
So What's the Best Approach?
AI tools can assist in the product design process, but they are not a replacement for human expertise. The best approach to improving your Shopify product design is to rely on experienced professionals who can diagnose issues, interpret data accurately, and apply creative solutions. AI can be a helpful tool, but it should not be the sole strategy for conversion rate optimization.
0 notes
Text
AI Workflow Automation: A Strategic Guide to Scaling Success

Organizations can boost productivity by 30–40% through strategic AI workflow automation implementation. But how do you ensure success at scale?
This comprehensive guide outlines four fundamental pillars for effective AI workflow automation:
1. Strategic Planning: Begin with thorough workflow audits, data quality assessments, and infrastructure evaluation 2. Seamless Integration: Select tools with robust APIs and scalable architectures 3. Quality Maintenance: Implement continuous monitoring and error detection systems 4. Future-Proofing: Design modular workflows and embrace self-improving AI capabilities
The key to success lies in starting small, measuring results, and scaling gradually. Organizations that follow this approach and thoroughly assess their capabilities are 2.3 times more likely to achieve their automation goals on time.
From selecting the right tools to maintaining security compliance, this guide provides actionable insights for businesses at any stage of their AI automation journey.
[Read the full article on Magai]
1 note
·
View note
Text
Top 7 Skills to Become A Full-Stack Developer in 2025
With the ever-increasing pace of technological change, the need for techies with multidisciplinary skills has never been higher. One of the most sought-after jobs in the tech field today is that of a Full-Stack Developer̶ one who could smartly trick both front and back-end development. By 2025, this position promises to be even more dynamic and skill-intensive than before, requiring the developers to be multi-talented, flexible, and always learning. Thus, whether you are just stepping into this profession or you're enhancing your skill set, full stack web development entails mastering as many skills as possible to stay relevant.
Let us check out the top 7 crucial skills that every full-stack developer should develop by 2025. Front-End Expertise The user interface is the first thing people see and interact with--that's why we call this front-end work fundamental. A full-stack developer must have a good working knowledge of HTML, CSS, and JavaScript, the trifecta of front-end development. For 2025, developers who know tools like React.js, Vue.js, and Next.js are in ever-increasing demand, as these frameworks can be used to develop dynamic, highly performant, and mobile-responsive web applications. One should also know a little about aspects such as responsive design and various browser compatibilities. Grasping concepts related to state management on the front end (for example, using Redux, Zustand, or the React Context API) boosts one's professional profile, with companies recognizing these competencies.
Strong Back-End Knowledge While the front-end sees what the user gets, the back-end makes things run in the background. Full-stack developers should command the lease on server-side programming using languages such as JavaScript (Node.js), Python (Django/Flask), Java (Spring Boot), or Ruby on Rails. You would need to know how to build RESTful APIs and work with user sessions, authentication, and authorization with communications to a database. Keeping in mind the social aspect of security and data integrity, it is also important for any practice to involve the rest-audit trail, validation, error handling, etc. Knowledge of cloud platforms like AWS, Google Cloud, or Azure would be an added advantage for deploying a scalable back end.
Database Management Every full-stack developer must have some hardcore database skills. It doesn't matter if it is the relational database world of MySQL or PostgreSQL or the advanced NoSQL world of MongoDB, you need to know how to work with schema design, efficient query writing, and database connection management. In 2025, a developer must know the difference between structured and unstructured data and know when to use what type of database. Indexing, normalization, and transactions will become especially critical to you as you build scalable applications. ORMs (Object Relational Mappers) like Sequelize or Mongoose are also crucial for streamlining code/database interaction.
Understanding of APIs APIs (Application Programming Interfaces) are the glue that binds together the various pieces of a system. A full-stack developer should be able to build and consume APIs. Although REST is still the most-used tool, GraphQL has emerged as an alternative technology due to its speed and flexibility. To properly build and solve any API issues, an understanding of Postman or Insomnia as tools is necessary. Familiarity with authentication methods, such as OAuth2.0, JWT (JSON Web Tokens), and API key management, secures your applications while they communicate with the different services.
Version Control Working on software projects without version control is akin to tight-rope walking without a safety net. Developers can use Git tools to track changes or collaborate more efficiently and roll back to previous versions and full-stack developers should know Git well enough to create branches and merge code to resolve conflicts and manage pull requests. Beyond 2025, GitHub, GitLab, and Bitbucket will be more relevant to the work process of the teams. Apart from collaboration, knowing Git shows the power and the discipline in practice concerning coding.
Performance Optimization Your web app must not just work, but also work fast. Performance optimization is nowadays inevitable in an era where user experience rules. On the front ends, such performance optimization encompasses reduced render time, reduced bundle size, lazy loading of components, or using CDNs. Back-end-side optimizations include the use of caching systems such as Redis, optimization in database query usage, and using effective server-side rendering methodologies. A full-stack developer should know how to use performance monitoring tools, such as Lighthouse and Google Web Vitals, and also backend profiling tools to identify and resolve bottlenecks.
Problem-Solving & Soft Skills: While technical skills are backbone assets in development, soft skills with problem-solving capabilities do much more to separate the wheat from the chaff in talented developers. This also includes proficiency in debugging codes and high-level thinking with systematic approaches toward solving problems in everyday development. Just as essential are communication, working as a team, and working in an agile environment. More and more, employers are looking for people who work as teammates but can also adjust easily to keep pace with ever-changing requirements, while contributing positively to the dynamics of a team.
Take up a Course: If in 2025, you really want to be a Full-Stack Developer, going for a regular course is going to be an accelerator in your skills. Make sure you find one that comes with hands-on projects, industry tools, and mentorship from seasoned pros. The course should be extensive — everything from HTML and JavaScript to back-end programming and deployment. Practical experience is the name of the game; the course should emphasize building an entire web application from scratch.
Conclusion Being a full-stack developer in 2025 will entail much more than just coding: it means knowing how every part of a web application fits together-from the user interface to the database. Mastering the above-mentioned seven basic skills will ensure your position as a really well-capable and competitive developer in today's technology-enriched world.
#fullstackdevelopercourseincoimbatorewithplacement#bestfullstackdevelopercourseincoimbatore#fullstackdevelopmenttrainingincoimbatore#javafullstackdevelopercourseincoimbatore#pythonfullstackdevelopercourseincoimbatore#fullstackwebdevelopmentcoursedetails#webdevelopmentcoursecoimbatore#advancedwebdevelopmenttrainingcoimbatore#learnfullstackwebdevelopmentintamil
0 notes
Text
WhatsApp Issue: Integration Challenges with Enterprise Systems
For enterprises seeking to leverage WhatsApp's massive user base and familiar interface, system integration represents one of the most significant technical challenges. While WhatsApp Business API theoretically enables connections between the messaging platform and enterprise systems, the reality often falls short of expectations. This WhatsApp issue creates substantial obstacles for businesses attempting to incorporate the platform into their broader technology ecosystem.
The WhatsApp Integration Issue Landscape
The fundamental WhatsApp issue stems from the platform's relatively closed architecture compared to purpose-built enterprise messaging solutions. Despite improvements to the WhatsApp Business API, organizations continue to encounter significant challenges when attempting to create seamless connections with critical systems like:
Customer Relationship Management (CRM) platforms
Enterprise Resource Planning (ERP) systems
Customer Service and Helpdesk solutions
Marketing Automation platforms
Business Intelligence and Analytics tools
Document Management Systems
Internal Communication platforms
These integration challenges represent a substantial WhatsApp issue that can undermine the platform's business value if not properly addressed.
Primary WhatsApp Issues in Enterprise Integration
1. Webhook Reliability and Message Delivery
A critical WhatsApp issue involves the reliability of its webhook system, which enterprises rely on to receive incoming messages and status updates. Organizations frequently report:
Delayed webhook delivery during high-volume periods
Inconsistent callback patterns requiring complex retry logic
Missing notifications for important status changes
Duplicate webhook deliveries requiring deduplication handling
These reliability issues create a significant WhatsApp issue for enterprise systems that expect consistent and timely event notifications.
2. Rate Limiting and Throughput Constraints
Another substantial WhatsApp issue involves the platform's strict rate limits, which can severely impact high-volume business operations:
Message sending throttling that limits burst communications
Conversation initiation restrictions that complicate marketing campaigns
Template message approval bottlenecks for time-sensitive communications
Quality rating impacts that can further reduce allowed throughput
For enterprises accustomed to controlling their communication infrastructure, these constraints represent a challenging WhatsApp issue that requires significant workflow adaptations.
3. Data Synchronization Complexities
Maintaining consistent data between WhatsApp and enterprise systems creates another significant WhatsApp issue:
Limited historical data access through official APIs
Challenges matching WhatsApp users with existing customer records
Complex conversation state tracking across systems
Media file handling and storage synchronization
Contact information management between platforms
These synchronization challenges often force enterprises to develop complex middleware solutions to address this WhatsApp issue.
4. Authentication and Security Framework Misalignment
Enterprise security requirements frequently conflict with WhatsApp's authentication approach, creating a WhatsApp issue where organizations must reconcile different security models:
WhatsApp's token-based authentication versus enterprise SSO systems
Challenges implementing fine-grained access controls
Difficulties auditing user actions within the WhatsApp environment
Limited integration with enterprise security monitoring systems
These security misalignments represent a significant WhatsApp issue that often requires specialized integration development.
5. Metadata and Context Limitations
A persistent WhatsApp issue involves the platform's limited support for rich contextual metadata:
Restricted custom attributes for message categorization
Limited conversation labeling capabilities
Challenges in maintaining conversation threading
Minimal support for business process context
For enterprises requiring rich metadata to drive automated workflows, this WhatsApp issue necessitates the development of external systems to maintain crucial context.
Business Impact of WhatsApp Integration Issues
These integration challenges create substantial business impacts:
Extended Implementation Timelines: WhatsApp projects typically require 30-50% more development time than comparable messaging integrations
Increased Development Costs: Specialized expertise requirements drive higher project expenses
Operational Inefficiencies: Staff often need to manually bridge gaps between systems
Customer Experience Inconsistencies: Information silos can create disjointed customer interactions
Analytical Blind Spots: Incomplete data synchronization limits business intelligence capabilities
For many enterprises, these consequences represent the true cost of the WhatsApp issue beyond simple technical challenges.
Strategic Approaches to WhatsApp Integration Issues
Despite these challenges, enterprises can implement effective strategies to address WhatsApp integration issues:
1. Middleware Development
Rather than attempting direct connections between WhatsApp and enterprise systems, successful organizations address this WhatsApp issue by developing specialized middleware:
Message Queuing Systems: Implementing robust queuing to handle webhook inconsistencies
Transformation Layers: Creating adapters that normalize data between WhatsApp and enterprise formats
State Management Services: Maintaining conversation context separate from WhatsApp
Retry and Resilience Logic: Building systems that handle communication failures gracefully
This abstraction layer approach effectively mitigates many aspects of the WhatsApp issue by isolating enterprise systems from the platform's integration challenges.
2. Certified Integration Partner Relationships
Another effective approach to this WhatsApp issue involves working with officially certified WhatsApp Business Solution Providers (BSPs):
BSPs often have prebuilt connectors for common enterprise systems
Their experience with WhatsApp's specific integration challenges speeds implementation
They typically maintain relationships with Meta that can help address critical WhatsApp issues
Their specialized knowledge can identify potential problems before they impact production systems
While this approach typically requires additional investment, it can significantly reduce the technical complexity of the WhatsApp issue.
3. Hybrid Communication Architecture
Some organizations address the WhatsApp issue by implementing hybrid architectures:
Using WhatsApp primarily for customer-facing communications
Maintaining separate systems for internal processes and data management
Creating limited, well-defined integration points rather than attempting deep integration
Developing clear boundaries for which processes belong in each system
This pragmatic approach acknowledges the WhatsApp issue of integration challenges but limits its impact on core business functions.
4. Comprehensive Testing Frameworks
Successful enterprises address this WhatsApp issue through robust testing:
Developing automated test suites specifically for WhatsApp integration points
Implementing continuous monitoring of WhatsApp API connectivity
Creating synthetic transaction testing to verify end-to-end functionality
Establishing performance testing regimes that simulate high-volume conditions
These testing approaches help identify potential WhatsApp issues before they affect production systems.
5. Phased Implementation Strategy
Rather than attempting comprehensive WhatsApp integration immediately, successful organizations often address this WhatsApp issue through phased approaches:
Beginning with limited use cases that demonstrate clear value
Gradually expanding integration points as expertise develops
Continuously refining the integration architecture based on operational experience
Building institutional knowledge before attempting more complex integrations
This measured approach helps manage the WhatsApp issue by limiting initial complexity while building valuable implementation experience.
Case Study: Overcoming WhatsApp Integration Issues
A large retail organization successfully addressed WhatsApp integration issues through a comprehensive strategy:
They implemented a dedicated integration layer between WhatsApp and their existing systems
They developed robust queuing systems to handle webhook reliability issues
They created a separate database for maintaining conversation context and customer relationships
They implemented comprehensive monitoring and alerting for integration points
Results included:
99.7% message delivery reliability despite webhook inconsistencies
Seamless customer context preservation across channels
42% reduction in customer service resolution times
Successful handling of seasonal volume spikes without degradation
Future Outlook for WhatsApp Integration
While integration remains a significant WhatsApp issue, several trends suggest potential improvements:
Meta continues enhancing the WhatsApp Business API with enterprise needs in mind
The growing ecosystem of integration partners is developing more sophisticated solutions
Third-party middleware platforms increasingly include robust WhatsApp connectors
Enterprise systems are adding native WhatsApp integration capabilities
These developments indicate that while the WhatsApp issue of integration challenges will persist, its severity may gradually decrease as the ecosystem matures.
Conclusion: Addressing the WhatsApp Integration Issue
The WhatsApp issue of enterprise integration challenges represents a significant but surmountable obstacle for organizations seeking to leverage the platform's reach and familiarity. By implementing thoughtful architectural approaches, working with experienced partners, developing appropriate middleware, establishing robust testing, and adopting phased implementation strategies, enterprises can successfully navigate these technical challenges.
Organizations that effectively address this WhatsApp issue position themselves to deliver superior customer experiences while maintaining operational efficiency. As WhatsApp continues its evolution from consumer messaging app to business communication platform, those who master its integration challenges gain significant competitive advantages in customer engagement and operational excellence.
0 notes
Text

ISAM Online Training Top & Best Rank of Banglore 2025
IBM Security Access Manager (ISAM) Online Training Top & Best Rank of Banglore 2025 is a robust identity and access management (IAM) tool that assists organizations in safeguarding their digital resources, securing user authentication, and applying access policies. ISAM offers centralized access control, multi-factor authentication, single sign-on (SSO), and support for cloud and on-premise applications, thus emerging as a vital security and compliance enhancement tool.Our ISAM Online Training is formulated to empower IT professionals, security administrators, and developers with skills to implement, configure, and manage ISAM efficiently. You can be either an IAM newbie or a veteran professional who needs to enhance skills; this course addresses all vital areas of IBM Security Access Manager.Introduction to IBM Security Access Manager (ISAM) Overview of Identity and Access Management (IAM) ISAM architecture and components Deployment options and system requirements User Authentication and Access Control Authentication mechanisms (password-based, multi-factor authentication) Configuring authentication policies and risk-based authentication Implementing Single Sign-On (SSO) Federated Identity Management Understanding Federation and SAML concepts Integrating ISAM with cloud-based applications Implementing OAuth, OpenID Connect, and JWT tokens Web and API Security Configuring Reverse Proxy for Web Security Protecting REST APIs using ISAM Implementing Web Access Control Policies ISAM Administration and Troubleshooting User Management and Role-Based Access Control Logging, Monitoring, and Auditing Security Events Debugging and troubleshooting ISAM configurations Integration with Other Security Solutions Connecting ISAM with LDAP and Active Directory Integrating ISAM with IBM Security Verify Customizing ISAM with Java and API Extensions Who Should Attend? Security professionals and IAM specialists IT administrators responsible for user access management Developers integrating authentication and authorization into applications Compliance officers ensuring regulatory security requirements Why Choose Our ISAM Online Training? Expert-Led Training: Learn from industry professionals with hands-on experience Comprehensive Course Content: Covers ISAM fundamentals to advanced security features Real-World Projects: Practical implementation of security solutions Flexible Online Learning: Self-paced and instructor-led training options available By the end of this ISAM Online Training, participants will gain in-depth knowledge of access management, authentication protocols, and ISAM configuration. This training prepares you for roles such as IAM Consultant, Security Administrator, and Access Management Specialist. Start your journey in identity and access management with our ISAM Online Training and enhance your cybersecurity skills today!
[email protected], +91-9148251978,+91-9008906809
0 notes
Text
How to Implement Staking and Yield Farming in Your DeFi Project
In the ever-evolving landscape of decentralized finance (DeFi), staking and yield farming have emerged as powerful mechanisms to attract liquidity and engage users. If you're building a DeFi project, implementing these features can significantly boost user adoption and create a sustainable tokenomics model. This comprehensive guide will walk you through the process of adding staking and yield farming capabilities to your DeFi project.

Understanding the Fundamentals
Before diving into implementation details, let's clarify what staking and yield farming actually entail in the DeFi ecosystem.
What is Staking?
Staking is the process where users lock up their tokens in a smart contract to support network operations and earn rewards in return. In DeFi projects, staking serves multiple purposes:
Protocol Security: In proof-of-stake networks, staked tokens secure the network
Governance Participation: Stakers often gain voting rights in protocol decisions
Reduced Token Velocity: Locking tokens reduces selling pressure
Passive Income: Users earn rewards for their commitment to the project
What is Yield Farming?
Yield farming takes the concept of staking further by incentivizing users to provide liquidity across various protocols. Farmers strategically move their assets between different platforms to maximize their returns, often earned through:
Trading Fees: A portion of transaction fees from DEX trades
Interest: From lending platforms
Token Rewards: Additional governance or utility tokens
Liquidity Mining: Special rewards for early liquidity providers
Planning Your Tokenomics
Before writing a single line of code, you need a solid tokenomics model that balances:
Token Utility: What purpose does your token serve beyond speculation?
Reward Sustainability: How will you fund rewards over the long term?
Distribution Schedule: What's the emission rate for reward tokens?
Lock-up Periods: How long should users stake to maximize rewards?
Remember, unsustainable APYs might attract liquidity initially but can lead to "vampire attacks" where users withdraw en masse once rewards diminish.
Technical Implementation Steps
1. Smart Contract Development
The foundation of your staking and yield farming system will be smart contracts. For effective implementation, you'll need to develop specialized contracts that handle:
Token staking with time-lock mechanisms
Reward calculation and distribution
Liquidity provider tracking
Emergency withdrawal functions
Governance integration
When designing these contracts, prioritize security, gas efficiency, and upgradeability. Most successful projects use established frameworks and libraries rather than building from scratch.
2. Reward Distribution Mechanisms
When designing reward distribution, consider these approaches:
Time-based Rewards: Tokens distributed based on staking duration
Amount-based Rewards: Larger stakes earn proportionally more rewards
Multipliers: Bonuses for longer lock-up periods
Declining Emissions: Gradually reducing rewards to ensure sustainability
3. Frontend Integration
Creating an intuitive user interface is crucial for adoption. Your DApp should include:
Wallet Connection: Support for MetaMask, WalletConnect, etc.
Staking Dashboard: Display staked amounts and earned rewards
APY Calculator: Help users estimate potential returns
Transaction History: Track staking and reward claiming events
4. Security Considerations
DeFi projects are prime targets for exploits. Protect your protocols with:
Thorough Audits: Engage multiple reputable auditing firms
Rate Limiting: Prevent flash loan attacks with time-based restrictions
Emergency Pause: Functionality to halt operations if issues arise
Timelock Mechanisms: Delay implementation of critical parameter changes
Real-world Examples and Best Practices
Successful Implementations to Learn From
Several DeFi projects have implemented staking and yield farming effectively:
Compound Finance: Their COMP distribution model rewards both lenders and borrowers
Aave: Offers staking for protocol governance and risk mitigation
Curve Finance: Uses vote-escrowed tokens (veCRV) for boosted rewards
SushiSwap: Introduced "Onsen" programs for targeted liquidity incentives
Common Pitfalls to Avoid
Learning from others' mistakes can save your project:
Impermanent Loss: Educate users about the risks of providing liquidity
Smart Contract Vulnerabilities: Avoid re-entrancy attacks and integer overflows
Centralization Risks: Ensure admin keys are managed securely
Economic Exploits: Consider game theory when designing incentives
Optimizing for Different Blockchains
While Ethereum remains dominant in DeFi, consider implementing on multiple chains:
Ethereum: Highest liquidity but expensive gas fees
BSC: Lower fees but more centralized
Polygon: EVM-compatible with fast, low-cost transactions
Solana: High throughput with different programming paradigm
Avalanche: Fast finality with EVM compatibility
Each blockchain has unique characteristics that may affect your implementation.
Regulatory Considerations
The regulatory landscape for DeFi is evolving rapidly. Consider:
KYC/AML: Whether your protocol should implement compliance measures
Securities Laws: If your tokens might be considered securities
Tax Reporting: How to help users track their rewards for tax purposes
Testing and Deployment Strategy
Before launching:
Develop Test Cases: Cover all possible user interactions
Deploy on Testnets: Test thoroughly before mainnet launch
Consider a Phased Rollout: Start with limited staking before full yield farming
Bug Bounty Program: Incentivize community security reviews
Conclusion
Implementing staking and yield farming in your DeFi project requires careful planning, robust smart contract development, and thoughtful user experience design. By balancing attractive incentives with sustainable tokenomics, you can create a thriving ecosystem that benefits both users and the long-term health of your protocol.
Remember that the most successful DeFi projects evolve over time. Start with solid fundamentals, listen to your community, and be prepared to adapt as the market and technology landscape changes.
Ready to start building? The DeFi space awaits your innovation!
#game#mobile game development#multiplayer games#gaming#metaverse#vr games#blockchain#unity game development
0 notes
Text
Google Cloud Security Best Practices for Businesses

In today’s digital-first world, businesses rely on the cloud to store, process, and analyze vast amounts of data. While cloud computing offers flexibility, scalability, and efficiency, security remains a major concern. Cyber threats are evolving, and companies must adopt best practices to safeguard their data and applications in Google Cloud.
Google Cloud provides powerful security tools and features, but businesses need to take proactive steps to enhance their security posture. In this blog, we’ll explore the essential best practices for securing your business on Google Cloud.
1. Implement a Strong Identity and Access Management (IAM) Strategy
One of the fundamental aspects of cloud security is ensuring that only authorized users have access to your resources. Google Cloud’s IAM allows businesses to control access permissions efficiently.
Best Practices:
Follow the principle of least privilege access—grant only the necessary permissions.
Use multi-factor authentication (MFA) to enhance security.
Regularly audit and review user permissions.
Implement service accounts with restricted permissions for applications.
By enforcing strict access controls, businesses can prevent unauthorized access and reduce the risk of data breaches.
2. Encrypt Data at Rest and in Transit
Data encryption is a crucial security measure to protect sensitive business information. Google Cloud provides default encryption, but businesses can enhance security further by managing their encryption keys.
Best Practices:
Enable Cloud Key Management Service (KMS) for enhanced encryption management.
Use TLS (Transport Layer Security) to secure data in transit.
Regularly rotate encryption keys and limit key access.
Encryption ensures that even if data is intercepted, it remains unreadable to unauthorized parties.
3. Enable Logging and Monitoring for Threat Detection
Monitoring activities within your Google Cloud environment helps detect and respond to security incidents in real-time. Google Cloud offers various security monitoring tools, including Cloud Audit Logs, Security Command Center, and Cloud Logging.
Best Practices:
Enable Cloud Audit Logs to track access and modifications.
Use Security Command Center to gain insights into vulnerabilities and threats.
Set up alerts in Cloud Monitoring for suspicious activities.
Regularly analyze logs to identify potential security threats.
A proactive monitoring approach helps businesses respond to incidents before they escalate into major security breaches.
4. Secure APIs and Endpoints
APIs are a common entry point for cyber threats, making their security a priority. Protecting APIs helps prevent unauthorized access and data leaks.
Best Practices:
Use API Gateway to manage and secure API traffic.
Implement OAuth 2.0 and API keys for authentication.
Enable rate limiting to prevent API abuse.
Regularly update and patch API vulnerabilities.
Securing APIs ensures that external and internal systems interact safely without exposing sensitive business data.
5. Adopt a Zero Trust Security Model
Zero Trust is a modern security framework that assumes no entity—internal or external—should be trusted by default. Google Cloud supports Zero Trust through BeyondCorp Enterprise.
Best Practices:
Require identity verification for all users and devices.
Implement context-aware access based on user roles, device health, and location.
Enforce continuous authentication instead of one-time logins.
Adopting Zero Trust reduces the attack surface and strengthens your cloud security posture.
6. Automate Security with Google Cloud Tools
Automation enhances security by reducing human errors and ensuring consistent enforcement of policies.
Best Practices:
Use Cloud Security Command Center to automate security assessments.
Enable Google Cloud Armor to protect against DDoS attacks.
Implement Workload Identity Federation for secure access to on-premises and multi-cloud environments.
Automate security patching using OS patch management.
Automation not only improves security but also allows businesses to focus on innovation without constant manual security interventions.
7. Ensure Compliance with Regulatory Requirements
Businesses must comply with industry regulations such as GDPR, HIPAA, and ISO/IEC 27001. Google Cloud offers compliance solutions to meet these standards.
Best Practices:
Use Google Cloud Compliance Reports to ensure adherence to regulations.
Enable Access Transparency to monitor Google’s access to your data.
Implement Data Loss Prevention (DLP) to detect and prevent sensitive data exposure.
Conduct regular compliance audits to address security gaps.
Meeting compliance requirements not only prevents legal penalties but also builds customer trust in your business’s security practices.
8. Protect Against Phishing and Social Engineering Attacks
Phishing attacks are a significant threat to cloud security. Businesses must educate employees and implement safeguards to prevent such attacks.
Best Practices:
Enable Google Workspace Security Center to analyze email threats.
Train employees on recognizing phishing attempts.
Use safe browsing and email authentication (SPF, DKIM, DMARC).
Implement endpoint security solutions to detect malicious activities.
User awareness and proactive defense mechanisms play a key role in mitigating social engineering threats.
9. Implement Disaster Recovery and Backup Strategies
A robust disaster recovery plan ensures business continuity in case of security incidents, data corruption, or natural disasters.
Best Practices:
Use Cloud Backup and Disaster Recovery services.
Implement multi-region replication for critical data.
Test disaster recovery plans periodically.
Set up automated backups with retention policies.
Having a strong backup and recovery strategy ensures that your business can quickly recover from any disruption.
10. Partner with a Google Cloud Services Provider
Securing your business on Google Cloud requires a combination of best practices, automation, and expert guidance. A Google Cloud Services Provider can help businesses implement security measures, manage compliance, and optimize cloud environments efficiently.
By following these security best practices, businesses can safeguard their cloud infrastructure, protect sensitive data, and build a resilient digital environment for growth.
By implementing these Google Cloud security best practices, businesses can confidently operate in the cloud while minimizing risks. Whether you’re a small startup or an enterprise, prioritizing cloud security ensures business continuity, compliance, and trust from your customers.
#Google Cloud security#cloud security best practices#cybersecurity#Google Cloud compliance#cloud security strategy#Google Cloud Services Provider
0 notes